Security researchers from Palo Alto Networks reported discovering malicous applications that were released to Google Play between October 2017 and November 2017.
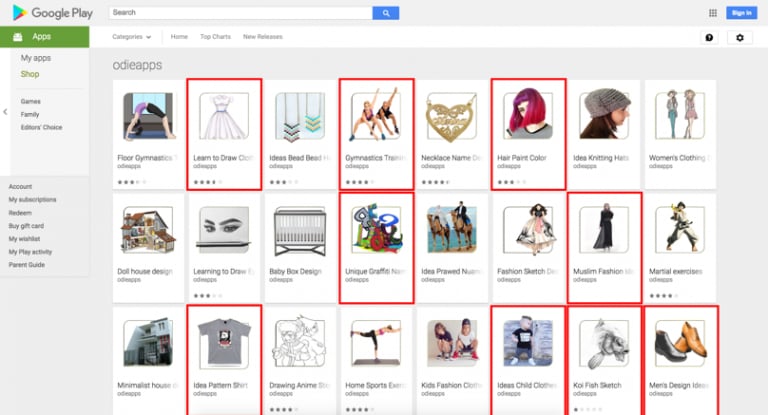
145 apps were deemed malicious by the team and were pulled from the Play Store. However, unusually, the applications did not contain malicious code intended for the Android mobile operating system. They were laden with malware intended for Windows machines.
These apps are no threat to Android devices — despite them being available for download in a repository of apps designed for that particular operating system. The code is “inert and ineffective on the Android platform,” according to Palo Alto, and will instead only run on Windows systems.
The following infected APK files were found on Google Play.
Recommendation
Despite being harmless for Android devices, it is still recommended to uninstall these applications if you already installed one of them.
Inspired by Paloalto Research
Les chercheurs en sécurité de Palo Alto Networks ont rapporté avoir découvert des applications malveillantes publiées sur Google Play entre octobre 2017 et novembre 2017.

145 applications ont été jugées malveillantes par l’équipe et ont été supprimées du Play Store. Cependant, les applications ne contenaient pas de code malveillant destiné au système d’exploitation Android. Ils étaient chargés de logiciels malveillants destinés aux machines Windows.
Ces applications ne constituent pas une menace pour les appareils Android – bien qu’elles soient disponibles au téléchargement dans une plateforme d’applications conçues pour Android. Le code est “inerte et inefficace sur les smartphones/tablettes Android”, selon Palo Alto, et fonctionnera uniquement sur les systèmes Windows.
Les fichiers APK infectés qui ont été trouvés sur Google Play sont les suivants:
| SHA256 | App Name |
| 1896ed8d12f5a7c3046acd929e64cc97e8acb020e40c1b3a2001b30003f50883 | Baby Room |
| 290b7f930361d06e8f8c93aa9f97405d6b4b9fef7f9ac13c3c73c8966cf0e83a | Motor Trail |
| b2fec79084611ad8abed3354399b2e759e903ec15976b9d10ac05e548964a1e9 | Tattoo Name |
| b828b870a317693a0ae0544b9d0ffddcf6442da4d1979f6f8ccafcbe5c96d1e3 | Car garage |
| 86661a4a611484f8db2593bfae241db9b53274a1736ec668335f878ed24795e4 | Japanese Garden |
| 79e77835c9690ca0bc6d376659dd15f50e396bbc573fcc7293d458d8002f6a60 | Koi fish |
| 91bb8594e118338f38de22e96e89cc5e11d619da3ec3dc0ecada13720111a588 | House Terrace |
| c41a8edaa85344e48a75843447358ea7a092fe1061bca79ac535abf467112eda | Skirt Design |
| 52d9df500ae7684d58c2bf65fb6852da1440e79b07a049f72585ccf8665e9d64 | Yoga Meditation |
| 21fce35139cfdf1145855987b6e3306adf26c3b60ba59b1c364a3d7d44bc5285 | Shoe rack |
| 4739a7d1317fee0a7a885a00468d9749bb7da5c5f1696408deaa736fa2aab6e9 | Unique T-shirt |
| bc49cec1896f7f4542ff8712da8475bf5e55abe7558918c260492467eb03ef6f | Mens Shoes |
| 7345975ca29d16e3b55309e84f6249990878482ed55e597269fdd0cb77a290ff | TV RuanG TaMu |
| ecb04d5359949bfbbc64fd7bedd8fde3a5b9703784fea8d758a3a643117165b0 | Idea Glasses |
| a21f4e9536dcbcd810fbfcdff8f6cce5b6338f1d5df7ba45abd1a5f4ed8dca76 | Fashion Muslim |
| 41386181f9e7dc8085d6a117607cd79346744d925e5d2ca67759742fbac47e51 | Bracelet |
| fceda65ea8624af018c072c60ed5fcb8b6bb00832fb63559e819463d2ba9db4e | Clothing Drawing |
| c5b24cf5d348a6fe3ad543f70379c7d9fa60a8e9bac03d6ea387fcdbcbbca932 | Minimalist Kitchen |
| c36e7566e2e92898162006b9922d9d8f450867224b67d2346f70d7e76b1cbae6 | Nail Art |
| 0039f9b2faac6146bddc2831fdfa6a03327f77d3954a1a27ab66e6b0b5952a3a | Ice cream stick |
| a8687cb35ee453958dc1757608505f3c5a7f137909f517acb7a850316d0e87b4 | Roof |
| 7da49a0122444b2087a582d142c82375541544fd765f29b9b3f7728e598b54e0 | Children Clothes |
| 7312c5ba59f89350b13fe93107233a06c79a68eedff0eb082ef7a5f24bec76e2 | Home Ceiling |
| bf00efc96cf3ecdd3069afbbfae53aeb79910848721fe50d64410760790f1a27 | PoLa BaJu |
| 892f883d3588ee952888cccb4bb9bb33092f1be924d981e69595a758daca8c86 | Living room |
| 5a1693d255e5f487214fd1cd46c0cff8d5375903459c7f87ae17f636fa470e32 | Bookshelf |
| 906cd586d8f7388c1fbb0581b926aa4b2dc5534d460cc3ba011198d26a1dfe16 | Knitted Baby |
| 96bd87c8bd8772b1f11b3e4771889b4d2d81739cd2ef7494a3ff54fc28e711f6 | Hair Paint |
| 54380fa8c12f6333a22fd0c728e615e92470565e96c7b39ae2f1d7e30584fc31 | Wall Decoration |
| b6671808dbc226c11697c54d000b6a30213478c141d96aa4c3d52fa5243cff16 | Painting Mahendi |
| 525c515e3e8c0d6007ab79f05a64c42951b440db4ab12f397218efa9692faa84 | Bodybuilder |
| 399058e95153600a471d94309a6c3e87f3851647fb003f6d4289fa5b5df389a4 | Couple shirts |
| 44066a23057ee93bed27737e8f444150c29c68b14bc9b21419f549188e436103 | Unique Graffiti |
| 1fcd61a10c170d259fca12e52d1930018adafad5613551b5bbb14987de1c7cfd | Paper flower |
| 0b85488788f7f83e879f41591d674b50d4daafb60094918391d98f143ba54ddc | Night gown |
| cb11dd259fa4fc0c1b4ee878cfb3c2df2a0a6ecab83276e33185ba7ce45c46ba | Wardrobe Ideas |
| 4091c8acea954fffd22be4c0675c440cf1fe4620d6659b8d23d8d3a2fc815e20 | Dining table |
| 9412ca41b7c9aebaeef05fe5c45bf5c5d998e5da44d5a7a495f5ba06c00feea0 | Gymnastics |
| 761032267b9659cd04676fce55e602a87e43cb4c75c58fa61486cc73da0016c6 | Use Child |
| 14bffba23e2bf4a61b4a54f1ef5027225290eab7f10d4c663570629e456cf51e | Window Design |
| 5dca7151c50ce88102b1fc5c0dd984c57202ad7c67f25be231d64cf1d52da437 | Hijab StyLe |
| 3350f4eb55c2f00c1ba0380044a1a6670a4eddc5cbabf903f2ad2e266eab58d2 | Wing Chun |
| c99a6e7e5d066076bacfad9142e3cf01855525782d638ccfe9ce7cd57d11ca5c | Fencing Technique |
Recommandation
Bien qu’inoffensif pour les appareils Android, il est toujours recommandé de désinstaller ces applications si vous en avez déjà installé un.
Inspiré par Paloalto Research






![[Securiday 2018] End User Protection](https://digitalys-mag.net/wp-content/uploads/2018/04/securiday18_conf.jpg)

![Détective Conan : les épisodes de l’histoire principale triées [part 1]](https://digitalys-mag.net/wp-content/uploads/2016/08/Meitantei.Conan_.full_.1913572.jpg)


![[Warning] Une faille critique dans tous les jeux Blizzard permettra aux Hackers de détourner des millions de PC](https://digitalys-mag.net/wp-content/uploads/2018/01/X1NH71Z11PTZ1508884994858.jpg)




