Vulnerability overview
Security researchers from Secura discovered a privilege-escalation vulnerability – dubbed “Zerologon”, CVE-2020-1472, that carries a critical severity rating from Microsoft as well as the maximum score of 10 under the Common Vulnerability Scoring System.
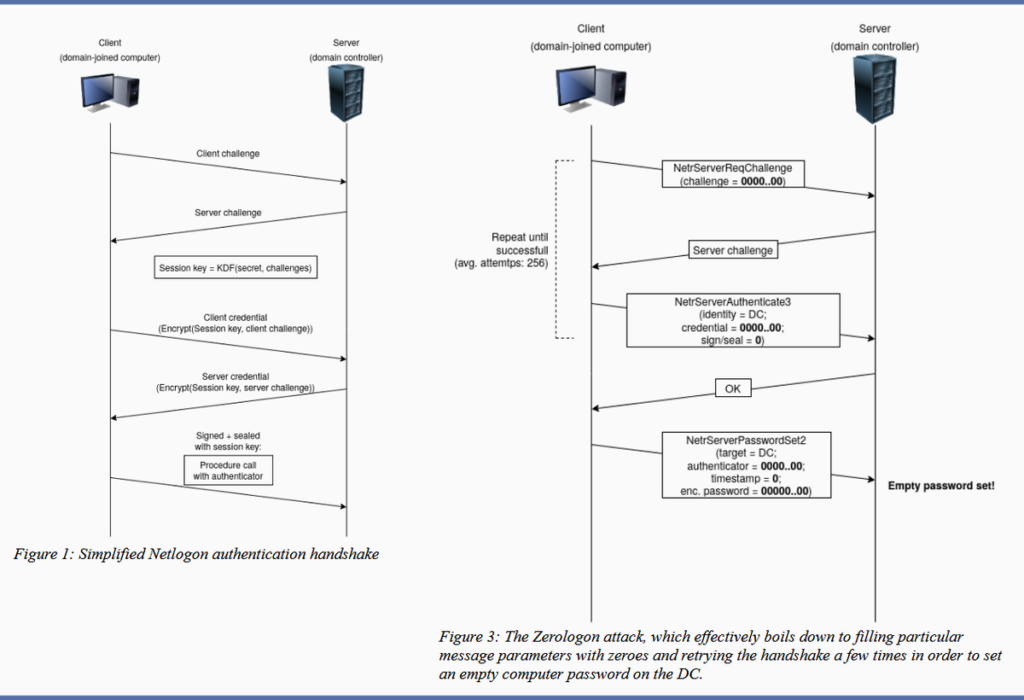
It was described as an elevation of privilege in Netlogon, the protocol that authenticates users against domain controllers.
Exploitation of this vulnerability is possible due to a flaw in the implementation of the Netlogon protocol encryption, specifically AES-CFB8. The vulnerability is triggered by sending a string of zeros to the Netlogon protocol. For this reason, it was dubbed “Zerologon”. (See the following graph)
The flaw allows anyone on a network utilizing the Netlogon protocol to elevate their privileges to that of the domain administrator.
This would allow an attacker access to the entire domain, opening up opportunities for further exploitation, data exfiltration, network disruption or whatever their objectives might be.
Affected systems
This vulnerability affects multiple Microsoft Windows Server operating systems:
- Windows Server 2008 R2 for x64-based Systems Service Pack 1
- Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
- Windows Server 2012
- Windows Server 2012 (Server Core installation)
- Windows Server 2012 R2
- Windows Server 2012 R2 (Server Core installation)
- Windows Server 2016
- Windows Server 2016 (Server Core installation)
- Windows Server 2019
- Windows Server 2019 (Server Core installation)
- Windows Server, version 1903 (Server Core installation)
- Windows Server, version 1909 (Server Core installation)
- Windows Server, version 2004 (Server Core installation)
Impact
Zerologon was described by many as the most dangerous bug disclosed this year. Attacks usually need to be carried out from internal networks, but if the domain controller is exposed online, they can also be carried out remotely over the internet.
“This attack has a huge impact, it basically allows any attacker on the local network (such as a malicious insider or someone who simply plugged in a device to an on-premise network port) to completely compromise the Windows domain. The attack is completely unauthenticated: the attacker does not need any user credentials.”
researchers with Secura wrote in a white paper
Exploits
The Secura researchers who discovered the vulnerability and reported it to Microsoft said they developed an exploit that works reliably, but given the risk, they aren’t releasing it until they’re confident Microsoft’s patch has been widely installed on vulnerable servers.
Security researchers from other security firms have published their own proofs-of-concept attack code (Examples of POC available: RiskSense, BlackArrow).
Microsoft said on Monday that Iranian state-sponsored hackers are currently exploiting the Zerologon vulnerability in real-world hacking campaigns.
The Iranian attacks were detected by Microsoft’s Threat Intelligence Center (MSTIC) and have been going on for at least two weeks, the company said today in a short tweet.
MSTIC linked the attacks to a group of Iranian hackers that the company tracks as MERCURY, but who are more widely known under their monicker of MuddyWatter.
The group is believed to be a contractor for the Iranian government working under orders from the Islamic Revolutionary Guard Corps, Iran’s primary intelligence and military service.
According to Microsoft’s Digital Defense Report, this group has historically targeted NGOs, intergovernmental organizations, government humanitarian aid, and human rights organizations.
The MERCURY attacks appear to have begun around one week after this proof-of-concept code was published, and around the same time, Microsoft began detecting the first Zerologon exploitation attempts.
Patches
Patching Zerologon was no easy task for Microsoft as the company had to modify how billions of devices are connecting to corporate networks, effectively disrupting the operations of countless of companies.
This patching process is scheduled to take place over two phases.
- First phase: took place on August 2020, when Microsoft released a temporary fix for the Zerologon attack.
- Second phase: a more complete patch is scheduled for February 2021, just in case attackers find a way around the August patches. Unfortunately, Microsoft anticipates that this later patch will end up breaking authentication on some devices. Some details about this second patch have been described here.
Recommendations & mitigations
Microsoft released a patch for the Zerologon vulnerability (CVE-2020-1472) as part of its August 11, 2020 Patch Tuesday security updates.
We highly recommend our readers to patch their domain controllers as soon as possible.
If you want to test your network for this vulnerability, you can use the Secura ZeroLogon testing script.
References
- https://www.secura.com/blog/zero-logon
- https://unit42.paloaltonetworks.com/zerologon/
- https://www.zdnet.com/article/zerologon-attack-lets-hackers-take-over-enterprise-networks/
- https://arstechnica.com/information-technology/2020/09/new-windows-exploit-lets-you-instantly-become-admin-have-you-patched/
- https://techcommunity.microsoft.com/t5/microsoft-365-defender/zerologon-is-now-detected-by-microsoft-defender-for-identity-cve/ba-p/1734034






![[Securiday 2018] End User Protection](https://digitalys-mag.net/wp-content/uploads/2018/04/securiday18_conf.jpg)

![Détective Conan : les épisodes de l’histoire principale triées [part 1]](https://digitalys-mag.net/wp-content/uploads/2016/08/Meitantei.Conan_.full_.1913572.jpg)


![[Warning] Une faille critique dans tous les jeux Blizzard permettra aux Hackers de détourner des millions de PC](https://digitalys-mag.net/wp-content/uploads/2018/01/X1NH71Z11PTZ1508884994858.jpg)




