Over the past three weeks, Steam, the popular game distribution platform, was facing a lot of criticism from the cyber-security community regarding their Bug Bounty policies.
It started with a responsible submission of zero-day vulnerability affecting Steam client to Valve’s bug bounty program on HackerOne.
The vulnerability was a local privilege escalation (LPE), tracked as CVE-2019-14743 , affecting the Steam client for Windows and that can allow an attacker with limited permissions to run a program as an administrator. With Steam having over 100 million registered users and millions of them playing at a time, this is a serious risk that could be abused by malware to perform a variety of unwanted activities.
However, Valve determined that the flaw was “Not Applicable” and the company chose not award a bug bounty or give an indication that they would fix it, and told the researchers that they were not allowed to disclose it.
Security researchers, who both recently discovered the same vulnerability and were told that Valve would not be fixing it because it was “out of scope” of their vulnerability reporting program, decided to publicly disclose it.
As result Vasily Kravets disclosed the vulnerability in a write up, and the second researcher named Matt Nelson decided to show how the vulnerability could be exploited and published a proof-of-concept PoC where he gets a command prompt window running with SYSTEM account privileges, the highest for a user on Windows.
Here is a 0day in Steam. This bug has been publicly disclosed (https://t.co/yQxqJUi9P3), so I’m opening up my PoC. No blog post since @PsiDragon covered it nicely. https://t.co/it7wAZbnF2
— Matt Nelson (@enigma0x3) August 7, 2019
After the massive outcry generated by this decision, Valve has changed its mind and released a fix. Unfortunately, though, another similarly reported vulnerability still exists.
While Valve may have fixed this one particular vulnerability (CVE-2019-15315) in the “Steam Client Service”, researchers still say that this was not a complete fix, though, and could be easily bypassed; this happened on August 15, when Twitter user Xiaoyin Liu posted that they had found a way around the fix.
I found a way to bypass the fix. The bypass requires dropping a file in a nonadmin-writable location, so I think it’s out-of-scope for Valve. Write-up: https://t.co/Lalum8LTvY cc @PsiDragon @enigma0x3 @steam_games #infosec #steam #bugbounty https://t.co/qIylEG7u2L
— Xiaoyin Liu (@general_nfs) August 15, 2019
Come August 20, Kravets tweets that he discovered another LPE (CVE-2019-15316) in the Steam client for Windows, but he could not report it because, after publishing his previous zero-day, he had been banned from Valve’s HackerOne bug bounty program.
Seeing that this vulnerability impacts only the Steam Windows client, with Steam having over 100 million registered users and 96.28% of them are running Windows according to the Steam Hardware & Software Survey: July 2019, the systems of roughly 96 millions of them are currently affected.
Valve banned me on their H1 program.
So…
I release new #ZeroDay #PublicDisclosure EoP vulnerability at Steam.
Another #0day.
Rus – https://t.co/jAoq5kCTfF
Eng – https://t.co/FfGXltXmpX— Felix aka [xi-tauw] (@PsiDragon) August 20, 2019
It would appear that these reports and public disclosures determined Valve to change things for the better and release a beta update for the Windows version of Steam, which should patch the reported LPE vulnerabilities.
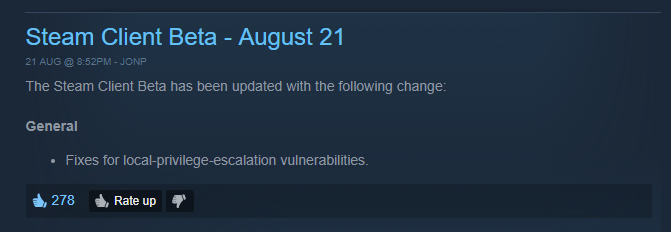
Valve also admitted their mistake to dismiss the bug reports and decided to update their HackerOne policy, to reflect that LPE vulnerabilities would now fall into the scope of its bug bounty program.
It remains to be seen how effective this new patch will be against the vulnerabilities, as Kravets tweeted that he would be waiting until the patch was released to the main client before testing.
https://t.co/WwHT7H8hcN
Valve is patching something. I’ll wait for main client update.— Felix aka [xi-tauw] (@PsiDragon) August 22, 2019
It also remains to be seen if Kravets will be unbanned from Valve’s HackerOne program and compensated for his discoveries.
Interesting readings related to this story:






![[Securiday 2018] End User Protection](https://digitalys-mag.net/wp-content/uploads/2018/04/securiday18_conf.jpg)

![Détective Conan : les épisodes de l’histoire principale triées [part 1]](https://digitalys-mag.net/wp-content/uploads/2016/08/Meitantei.Conan_.full_.1913572.jpg)


![[Warning] Une faille critique dans tous les jeux Blizzard permettra aux Hackers de détourner des millions de PC](https://digitalys-mag.net/wp-content/uploads/2018/01/X1NH71Z11PTZ1508884994858.jpg)