This year’s edition of Verizon Data Breach Investigations Report comes out with an of analysis 41,686 security incidents, of which 2,013 were confirmed data breaches with data provided by 73 sources. It has big focus on state-sponsored attacks and cyber-espionage. “Cyber-Espionage is rampant in the Public sector, with State-affiliated actors accounting for 79 % of all breaches involving external actors”.
First, let’s define Breach and Incident to avoid any potential misunderstanding.
Incident: A security event that compromises the integrity, confidentiality or availability of an information asset.
Breach: An incident that results in the confirmed disclosure—not just potential exposure—of data to an unauthorized party. So, basically, it includes only the incidents in which data was actually compromised.
What are some of the most interesting takeaways from Verizon’s latest annual security report?
The DBIR validated a lot of the things security professionals already knew. For example, the fact that the majority of attacks are carried out by outsiders.
- 69% were external attacks.
- 34% of attacks involved an internal actor. Which means that the person standing next to you at the coffee machine could be stealing company data or working with someone externally to steal company data.
“What are the bad guys doing?”
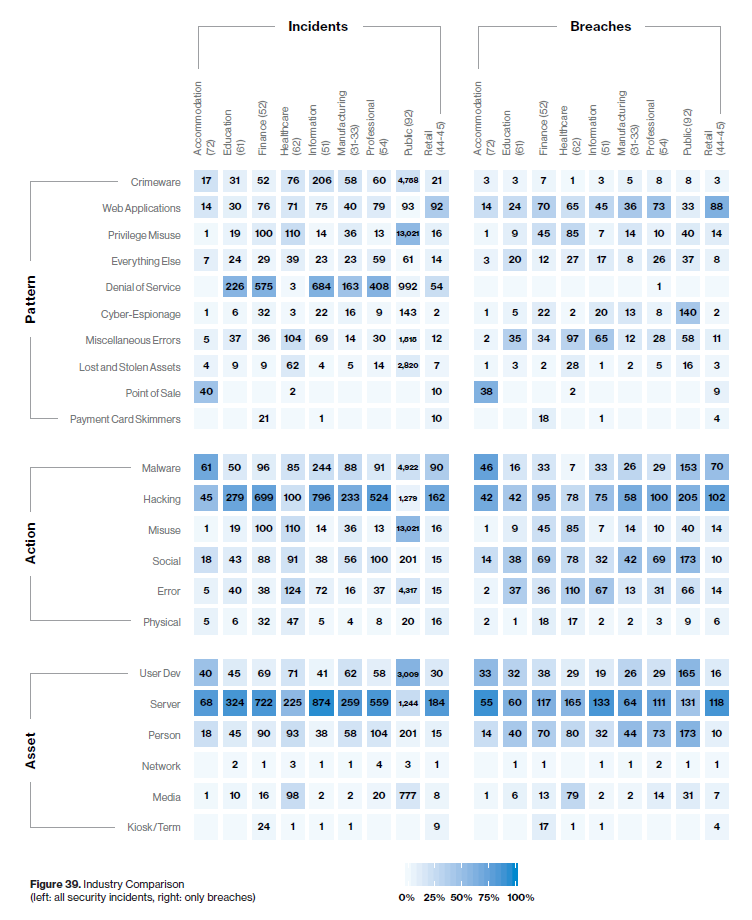
A quick glance at the figure below (Figure 12 from the report), phishing and the hacking action variety of use of stolen credentials are prominent fixtures.
- From the same figure, Only 6% of breaches in our data set this year involved exploiting vulnerabilities.
Broken myth
In the past, several security professionals assumed that only a fraction of companies needed to worry about state-sponsored attackers. After reading the report, it looks like even small businesses are now targets if they have information that someone wants.
- 23% of bad actors are identified as nation-state or state affiliated compared to just 12% in the 2018 report.
While nation-state groups are often described as sophisticated actors with advanced skills and tools, the Verizon DBIR said:
- 78% of cyberespionage-related incidents involved phishing.
“The purpose of this study is not to rub salt in the wounds of information security, but to contribute to the ‘light’ that raises awareness and provides the ability to learn from the past,” Verizon’s research team wrote in the report.
To read the full DBIR report click here.






![[Securiday 2018] End User Protection](https://digitalys-mag.net/wp-content/uploads/2018/04/securiday18_conf.jpg)

![Détective Conan : les épisodes de l’histoire principale triées [part 1]](https://digitalys-mag.net/wp-content/uploads/2016/08/Meitantei.Conan_.full_.1913572.jpg)


![[Warning] Une faille critique dans tous les jeux Blizzard permettra aux Hackers de détourner des millions de PC](https://digitalys-mag.net/wp-content/uploads/2018/01/X1NH71Z11PTZ1508884994858.jpg)